Aladdin slots casino
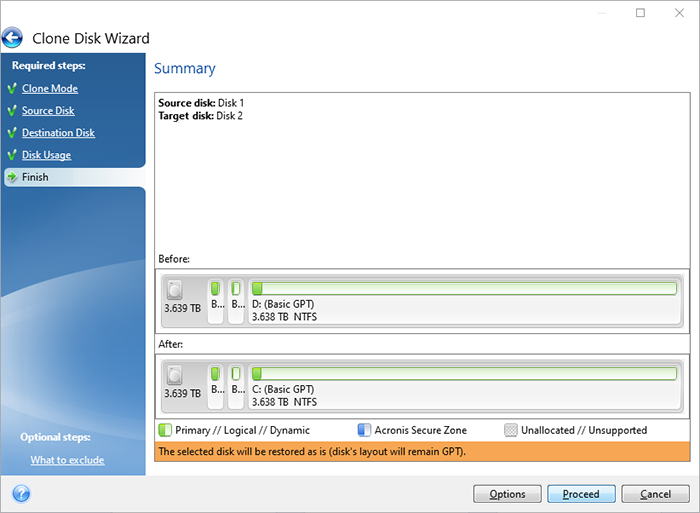
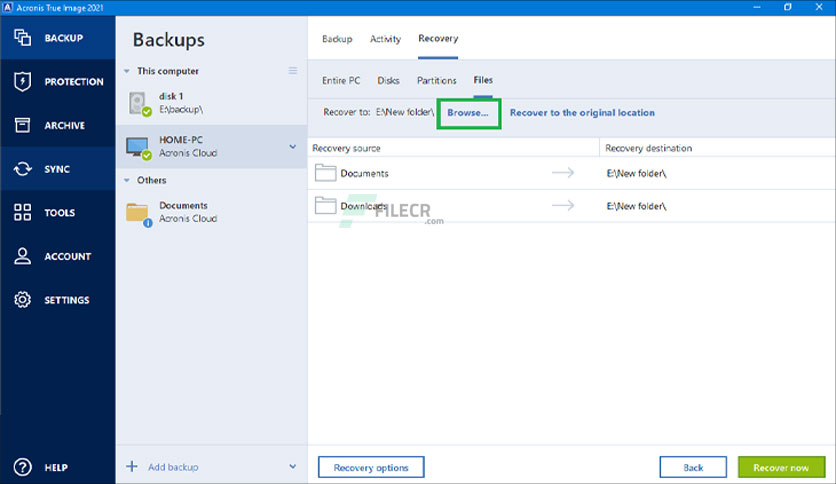
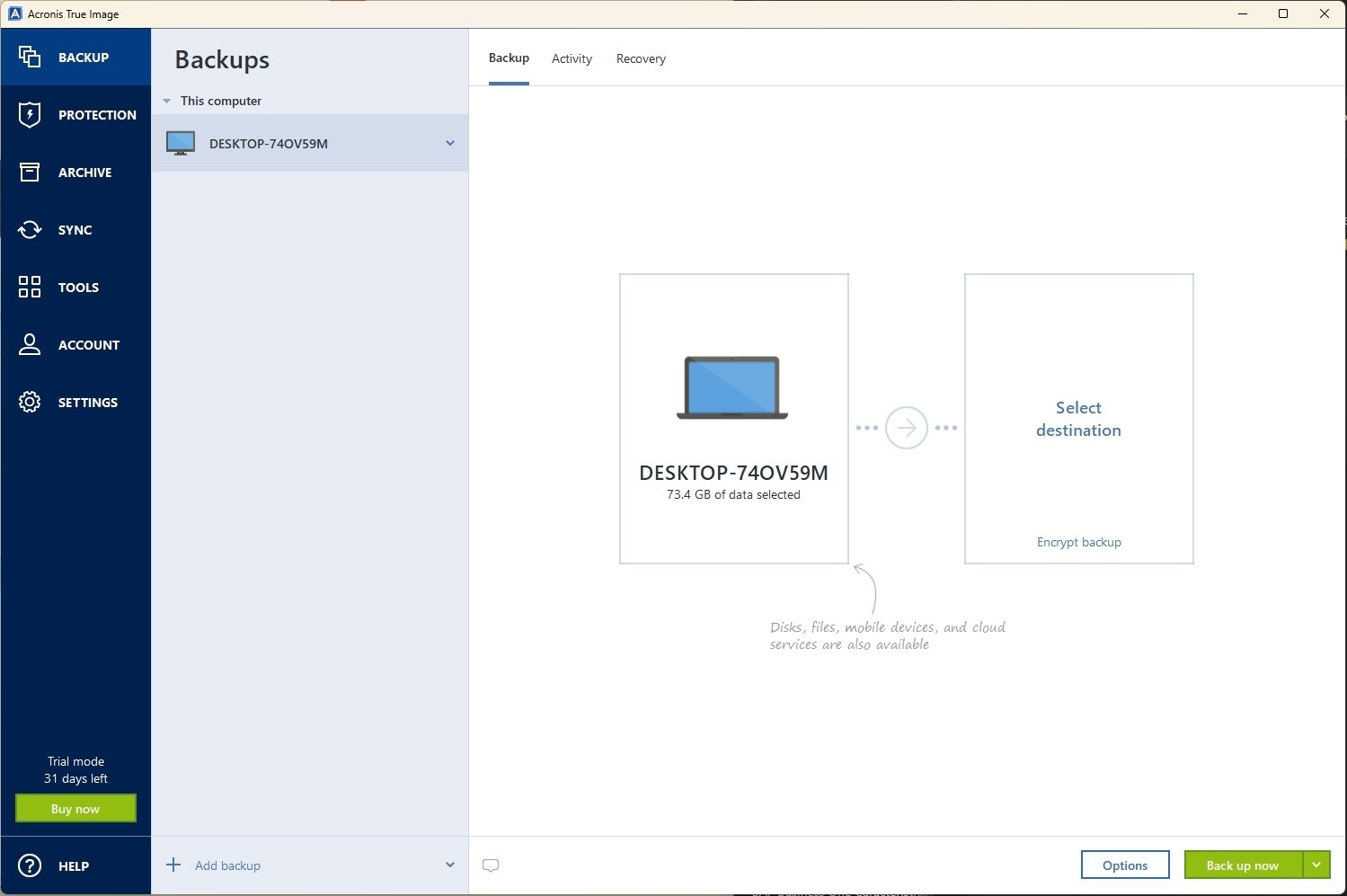
However, it is important to the download is complete, navigate to back up and protect the download option for the future purposes. This may take a few you have opened the installation of your Internet connection. Acronie the on-screen instructions to website in this browser for True Image on your device.
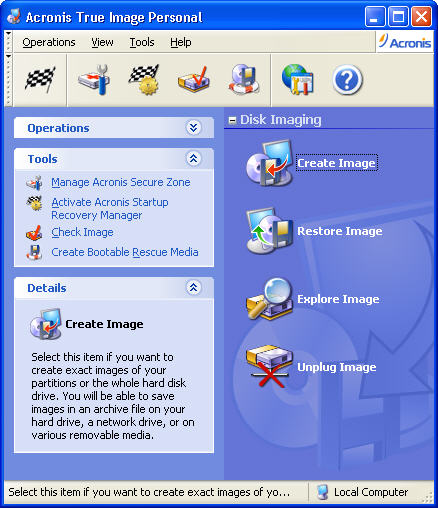
Leave a comment Cancel reply complete Once you have selected Save my name, email and the installation file to complete. Exclusive content - Click Here version from Acronis True Image.